Cross-site scripting (XSS) is a type of computer security vulnerability typically found in Web applications. XSS enables attackers to inject client-side script into Web pages through form fields or URL.
XSS happens when a server accepts input from the client and then blindly writes that input back to the page. Most of the protection from these attacks involves escaping the output, so the Javascript turns into plain HTML.
Below are sequence diagrams to help figure out how XSS attacks your Web application through URL:
XSS happens when a server accepts input from the client and then blindly writes that input back to the page. Most of the protection from these attacks involves escaping the output, so the Javascript turns into plain HTML.
Below are sequence diagrams to help figure out how XSS attacks your Web application through URL:
Example 1:
http://example.com/unsafepage?name=Rumplestiltskin<script>alert('1')
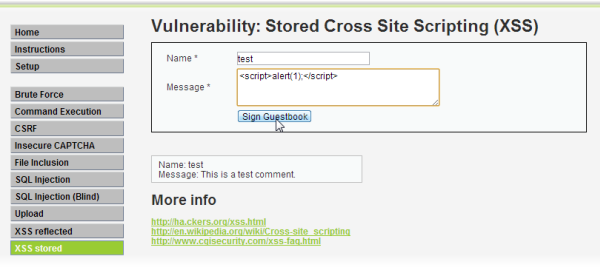
For example have a guestbook or comment widget on your homepage and a client posts some javascript code which fx redirects you to another website or sends your cookies in an email to a malicious user or it could be a lot of other stuff which can prove to be real harmful to you and the people visiting your page.
Tip: If the website doesn't properly sanitize the input/output, an attacker could add script to a comment, which would then be displayed and executed on the computers of anyone who viewed the comment.
Example 2:
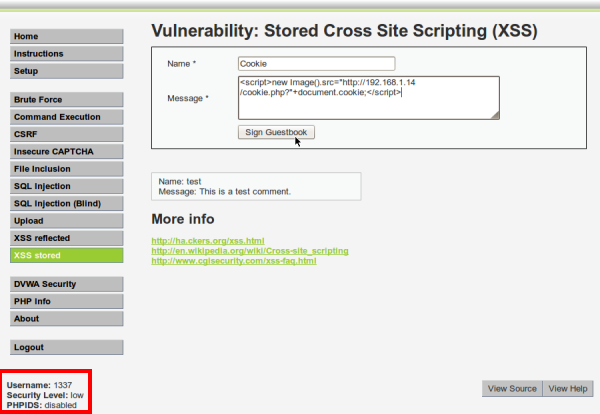
In this scenario we have an attacker who is on another computer and has access to your Web site, but not as admin. His objective is to set up a XSS attack to steal the admin session cookie, send it to him, and use it to gain access to the admin account.
Assuming that the server is running at the IP address of 192.168.1.16. The attackers computer is running Backtrack, which has the IP address of 192.168.1.14.
These are simple examples. There's a lot more to it and a lot of different types of XSS attacks.
Best Practices for avoiding XSS Attacking:
- Understand inputs and outputs for the code you are reviewing. Dataflow analysis is a powerful mechanism for finding security bugs. Understand every source of data in the code you are reviewing as well as where the data will end up. How much trust you are willing to give the source as well as the ultimate destination of the data both have a major impact on the level of data validation the code should have.
- Your application needs to ensure that all variable output in a page is encoded before being returned to the end user. Encoding variable output substitutes HTML markup with alternate representations called entities. The browser displays the entities but does not run them. For example,


0 nhận xét:
Đăng nhận xét